Key Generation and Certificate Signing Request (CSR)
Creating a private key and requesting a certificate (public key) can be solved in OpenSSL with a single command and entering the necessary information. Certificate request (CSR) and private key generation can also be easily performed in the SSLmentor customer administration.
OpenSSL
To work with certificates, you need to have the OpenSSL library installed. See the OpenSSL for Windows and Mac OSX page for instructions and download links.
Generating a certificate request (CSR) and private key
The command creates a private key as well as a certificate request. You must specify a path to place the files in another directory.
openssl req -new -newkey rsa:2048 -nodes -out request.csr -keyout private.key
For key generation and certificate requests, it is important that the request contains the correct information. Selecting rsa: 2048 means setting the key length. For higher security, it is possible to set rsa: 3072 or rsa: 4096.
Important! You must always fill in the domain name and country code according to the ISO standard. Leave the item "A challenge password" empty!
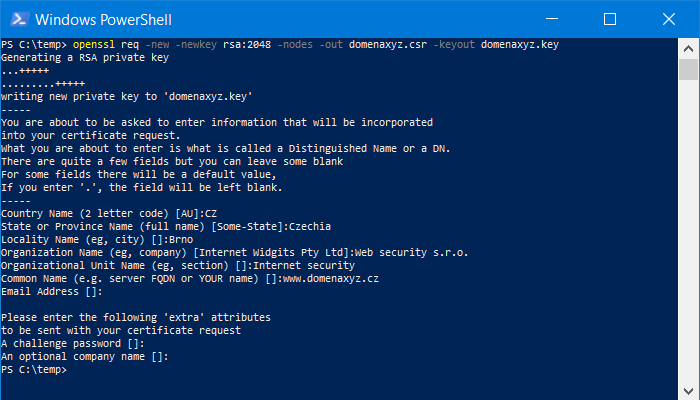
Certificate Request Verification (CSR)
To verify that the CSR (Certificate Signing Request) is correct, we can run the command with the "-verify" parameter added. It is advisable to perform verification before sending the request to the certification authority. Alternatively, we recommend testing your CSR using the tool by DigiCert - Check your CSR.
openssl req -in request.csr -text -noout -verify
Information entered in the certificate request
The following information is entered when generating the keys (an example of filling in is given after the arrow).
- Common name [CN]: domain name -> www.sslmentor.com
- Organization [O]: exact company name, domain owner -> Web security s.r.o.
- Organizational unit [OU]: company department -> internet / eshop / it / ...
As of Sept 1, 2022, public TLS certs will not have an OU, and will ignore OU. - City/locality [L]: city -> Prague
- State/province [S]: -> Czech republic
- Country/region [C]: country code according to ISO -> CZ
- Key Size: 2048 bit
We recommend entering the domain name exactly as it is set on the server and it is displayed in the browser. Although certification authorities insert both variants into the certificate (with and without www before the domain name), both variants are not inserted for multi-domain certificates.
The maximum number of characters for Common name [CN] and Organization [O] is 64. You can find more rules on the Baseline requirements and RFC 5280 Violations.
Country/region [C]:
- GB - Great Britain
- IE - Ireland
- US - United States of America
- DE - Germany
- CZ - Czech republic
- HU - Hungary
- AT - Austria
- PL - Poland
The country code must be entered exactly according to ISO in CAPITAL LETTERS.
An overview of ISO country codes can be found on the website of the International Organization for Standardization www.iso.org.
What is a Challenge password?
When generating the certificate, the entry "A challenge password" is offered. Always leave blank, otherwise the CA will reject the order. The challenge password is defined in RFC 2985 as the certificate revocation password.
Minimum information for DV certificates
Domain certificates (DV) contain only domain information and all other data entered in the application is deleted by the certification authority.
For example, the information in the SSL body of the PositiveSSL certificate is only:
- CN = domain.com
- OU = PositiveSSL
- OU = Domain Control Validated
The minimum information that must be entered for domain certificates in order for a certificate to be issued is Common name [CN] and Country/region [C]. However, we recommend that you fill in all the information due to a possible rejection by a certification authority.
Where next?
Back to Help
Found an error or don't understand something? Write us!






