CAA record
The Certification Authority Authorization (CAA) DNS Resource Record allows a DNS domain name holder to specify the Certification Authorities (CAs) authorized to issue certificates for that domain. Publication of CAA Resource Records allows a public Certification Authority to implement additional controls to reduce the risk of unintended certificate mis-issue.
Record also allow you to set notification rules when someone requests a certificate from an unauthorized CA. Placing CAA record in a DNS domain is another way to enhance Internet security.
What is CAA record
A CAA (Certification Authority Authorization) record is a record in the DNS zone of a domain that tells which certification authority is allowed to issue SSL certificates to the domain. If no CAA record is listed in the DNS, each CA can issue a certificate for that domain. If a CAA record is present, only the CAs listed in the records may issue certificates for the domain. CAA records can set domain-wide policies or specific names. CAA records are also inherited by subdomains, so a CAA record inserted into example.net will also be valid on any subdomain, such as subdomains.example.net.
- CAA records are specified in RFC 6844.
- In March 2017, the obligation to check CAA domain records was voted on in the CAB forum, and as of September 8, 2017, all public CAs are required to check CAA domain records before issuing a certificate and reject the certificate request if the CAA record exists and the CA is not listed there.
CAA record values
The canonical presentation format of the CAA record is: CAA <flags> <tag> <value>
- <flags> (0 – 255) The default is 0 (required). If you put 1, this blocks the validation if the tag is unknown by the CA. We recommend setting to "0".
Each CA can further specify its own parameters in terms of values. - The <tag> parameters
- issue allows the issuance of all types certificates from specified CA
- issuewild allows you to allow the issuance of WildCard certificates separately
By specifying 0 issuewild ";" we indicate that no WildCard certificates should be issued on the domain
The issuewild property has the same syntax and semantics as the issue property except that issuewild properties only grant authorization to issue certificates that specify a wildcard domain and issuewild properties take precedence over issue properties when specified. - iodef sets the email address or Web service address for reporting policy violations listed in CAA records by a certification authority
- <value>
Example of CAA record format in DNS:
- Domain Type Value | note
- sslmentor.com. IN CAA 0 issue "sectigo.com" | certificate can be issued by CA Sectigo
- sslmentor.com. IN CAA 0 issue "letsencrypt.org" | certificate can be issued by Let’s Encrypt
- sslmentor.com. IN CAA 0 issuewild "sectigo.com" | ONLY CA Sectigo can issue a Wildcard certificate
- sslmentor.com. IN CAA 0 iodef "mailto:info@sslmentor.cz" | contact for notification of violations
How to set CAA record
Before we place a CAA record in the DNS zone, it is advisable to generate it using one of the online services. One such tool is SSLMate (CAA Record Helper), which offers a choice of many certification authorities. All you have to do is choose your preferred authority, whether you can issue any certificate or even a WildCard, and the generator will offer records for insertion into the DNS.
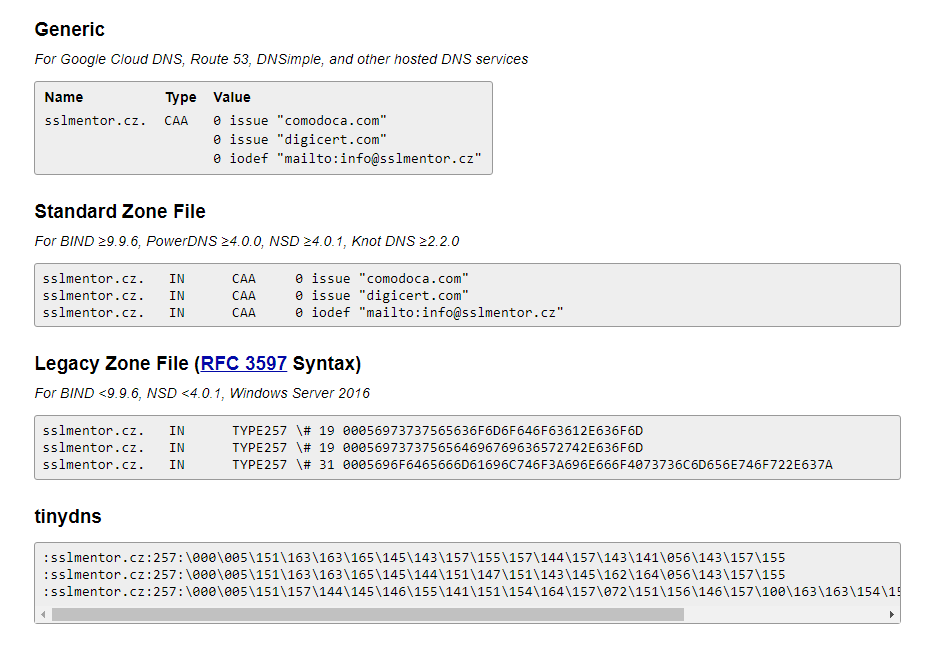
Inserting CAA record into DNS
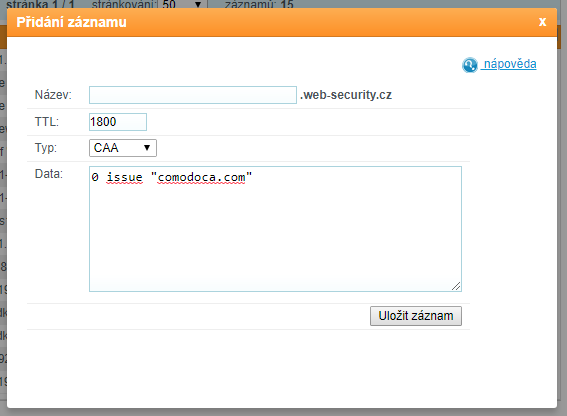
In order to insert a CAA record, the DNS record provider must support it. Nowadays, every hosting or registrar should offer to enter CAA records in DNS. The pictures show the insertion at some hosting services. It is always necessary to wait for it to expand after inserting CAA records. If hosting requires it, don't forget to have new DNS records published to the Internet. For example, you must confirm "Apply changes".
Checking CAA record
As DNS records expand, we can use some of the online tools to check if we have successfully uploaded CAA records. For example, dnsspy.io/labs/caa-validator or by listing a CAA record in DNS with digwebinterface.com
Where next?
Back to Help
Found an error or don't understand something? Write us!






